Protect your Contact Center Data with ice
by Shaundalee Carvalho | Published On June 2, 2021
Slice of ice Recap: Security and Standards – Mitigating Security Risks On Wednesday, May 19th, ComputerTalk presented their latest Slice of ice webinar, Security and Standards – Mitigating Security Risks. In this session, Jason Ellis of the Sales Operations team discussed risks and challenges, security protocols, and the power of ice.
Click here to watch the full recording of the session.
Risks and Challenges
In our ever-changing world, new security risks are continuously being identified. Security standards exist to help mitigate these risks, but it's important to know what kind of concerns we should be looking out for. Some areas of concern include:
- Data security – In today's digital world, we need to know where our data is residing, how it gets there, and who has access to it.
- Payment card transactions – There is an inherent risk to any online transaction. When a consumer gives their payment card number to a merchant virtually, there is potential for the card to be stolen and used fraudulently.
- Data privacy and support of privacy legislation – Data privacy involves both of the first two points. If you give your card number to a contact center rep, you may wonder if anyone at that company can then go and find it. Since privacy legislation is ever-changing, businesses must also ensure that they are up to date on industry standards.
- Disaster recovery and business continuity – Businesses must have plans in place for how they will continue day-to-day operations in a worst-case scenario, such as servers being compromised or office spaces being blocked.
Having detailed plans and policies to address these concerns is the most important thing a business can do for security. In addition to the everyday concerns mentioned above, there are some COVID specific security concerns that businesses face in today's world.
When many organizations sent their employees to work from home at the start of the COVID-19 pandemic, those who were not prepared for remote work were left scrambling to come up with policies to ensure security was not compromised. Remote work means that employees are not utilizing the secure office network. Supervisors are also finding it more difficult to manage day-to-day operations without being able to see their agents. If employees are using potentially unsecure devices, there is even greater need for security.
Security Protocols
Considering all these security risks, it's essential to follow security protocols. Some of these protocols include Payment Card Industry Data Security Standard (PCI-DSS), Service and Organization Controls (SOC 2), and the Microsoft 365 App Compliance program. Each audit is conducted differently and focuses on different core features. However, each of these compliances share the following characteristics:
- Comprehensive information security framework
- Secure development policies
- Strict change management practices
- Regular patching, scans, and testing
- Annual evidence-based third party validation
Payment Card Industry Data Security Standard (PCI-DSS)

The Payment Card Industry Data Security Standard, also known as PCI-DSS, is administered by the Payment Card Industry Security Standards Council. It is a set of cybersecurity controls and business practices that applies to "any entity that stores, processes, and/or transmits cardholder data." This includes virtually any organization that sells anything or accepts donations. PCI-DSS is used to ensure that payment card numbers remain secure as they are transmitted across the economic ecosystem. PCI compliance is achieved through an evidence-based audit and must be re-certified year after year.
Service and Organization Controls (SOC 2)

Service and Organization Controls, also known as SOC 2, is a technical audit performed by a third-party auditor. It is a data security and privacy framework established by the American Institute of Certified Public Accountants (AICPA). SOC 2 is used to test whether your service organization controls meet the stringent requirements of the SOC privacy and security framework. It is based on 5 trust principles. The protocol applies to any organization that wants to ensure the security, availability, processing, integrity, and confidentiality of customer data. SOC 2 certification comes in 2 stages. A Type 1 report, typically an organization's first certification, looks at internal controls, data governance, security, and privacy at the time of the audit. Type 2 reports on the effectiveness of those controls since the company's previous audit, typically one year earlier.
Microsoft Teams Certification

Validation of security controls was required for ice Contact Center to achieve its status as a Microsoft Teams Certified contact center. The Microsoft 365 App Compliance program is a three phase approach to app security and compliance within Microsoft 365 applications. It involves Publisher Verification, Publisher Attestation, and finally, Microsoft 365 Certification. It applies to any organization with an application looking to integrate with a product in the Microsoft 365 ecosystem. The 4 sectors that Microsoft examines when certifying a solution are application security, operational security/secure deployment, data handling security and privacy, and an optional external compliance framework. The certification is used to offer assurance and confidence to organizations that data and privacy are adequately secured and protected when using Microsoft Teams applications
What ComputerTalk Does
ComputerTalk has achieved all of the above certifications. We have been PCI-DSS certified since 2013, and SOC 2 certified since 2019 (currently with a Type 2 certification). We have been a Microsoft Gold partner since 2005, and we recently became one of the first to achieve the Microsoft Teams Certification for Contact Center. Customer security is at the forefront of every decision ComputerTalk makes.
What Your Organization Can Do
Every organization can take steps to improve their overall security. Such steps include:
- Strong password management – ice offers a customizable password policy for users or the ability to use single sign-on. Businesses can choose how this is enforced.
- Cybersecurity training – You can help protect your organization by keeping your employees well-trained in cybersecurity. ComputerTalk conducts security training in every department.
- Security checks on new hires and resources – Organizations can also protect themselves by conducting police background checks or other checks on new hires.
- Organization-wide initiative – Make security an organization-wide initiative. Everyone must do their part. You can help this mission by creating a cross-functional team for security requirements.
The Power of ice
icePay
icePay, one of our standalone applications, is used to securely accept payments to your organization without disclosing card details to the agent.
For example, suppose John wants to rent a canoe from a retail store. He calls the store and is connected to Sara in the rental department. Sara walks John through the rental details. When it's time to collect a payment, Sara clicks the icePay button on her iceBar. When the icePay window opens, Sara fills in the payment amount and then clicks Conference to start the icePay application with John.
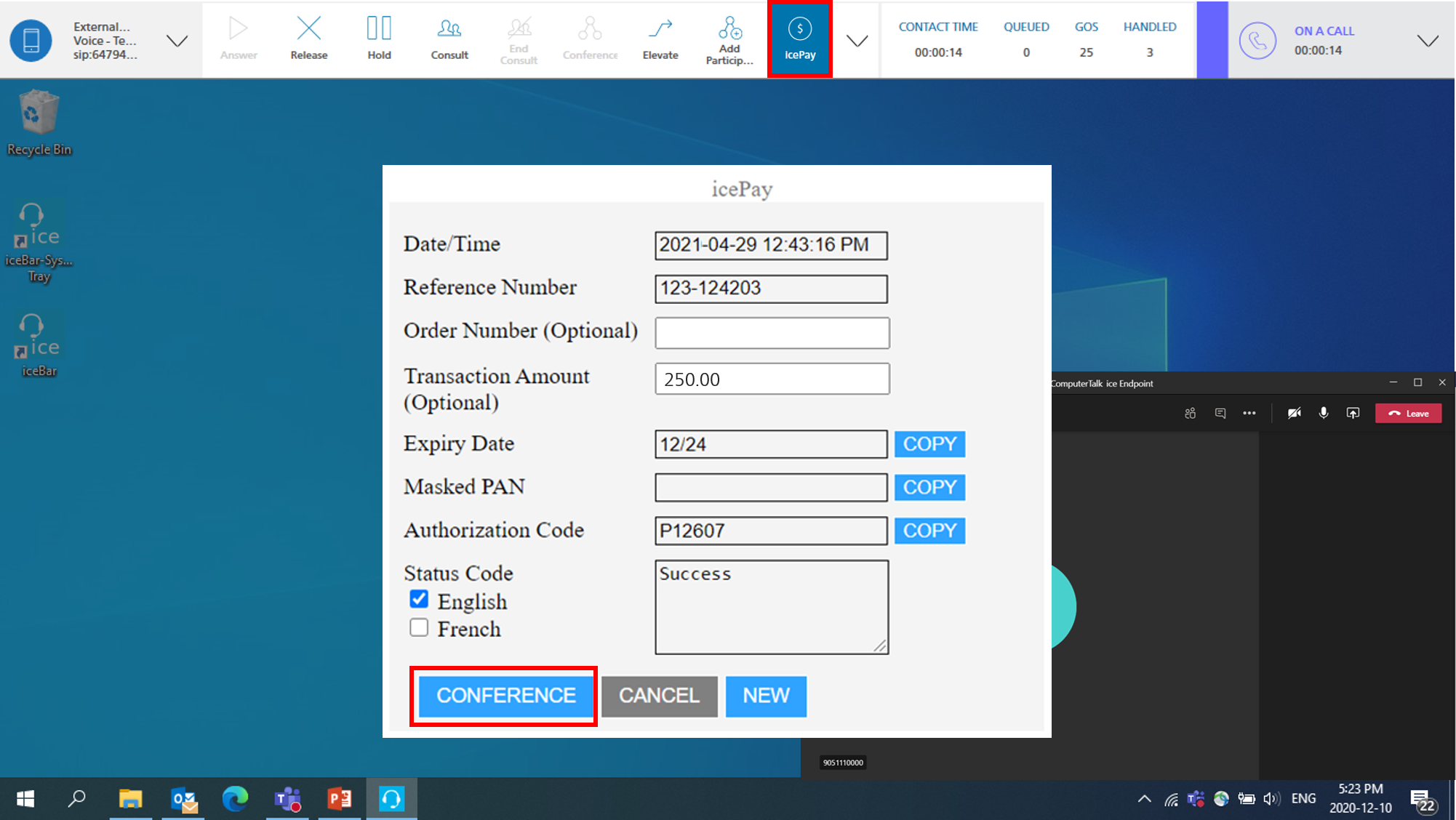
From there, John will be prompted through a self-service application to complete the payment securely. Sara will remain on the call to assist John if he has any problems, but the card information will not be disclosed to Sara at any point. The icePay window will be updated when the transaction is confirmed. Sara can then finalize the details of the rental with John.
Data Encryption
While the icePay application is designed specifically for secure payment processing, data encryption is a standard for all interactions within ice.
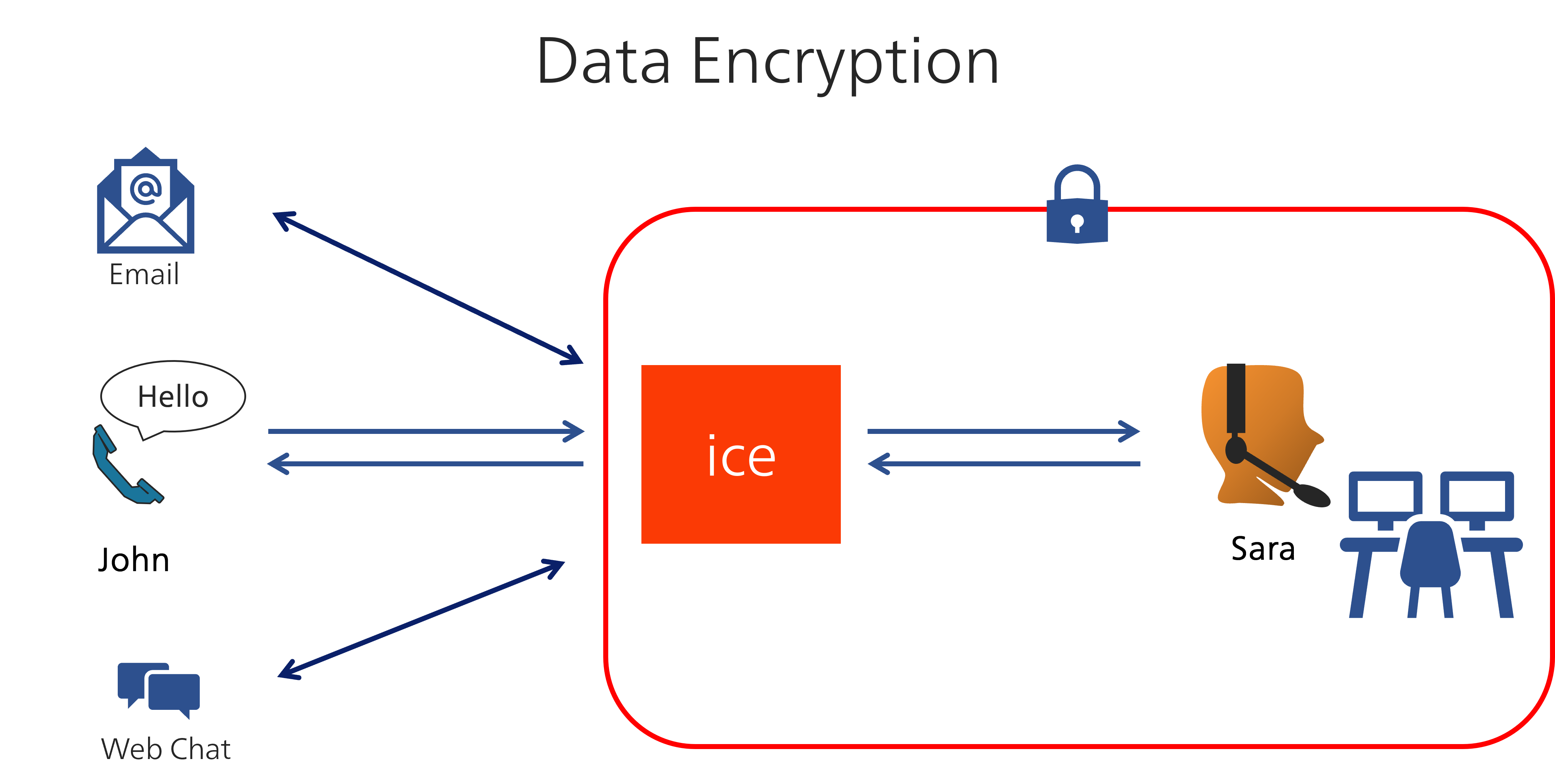
When John calls and speaks to Sara, the data is encrypted both on the way to the agent and back to the caller. This applies to email and IM contacts as well.
Security concerns are constantly evolving. ComputerTalk will continue to exceed industry standards to ensure your data is always secure.
To learn more, contact your account owner or request a demo. Our next Slice of ice session will be on June 16th at 12:00 PM ET. Register to learn about iceChat.
More from our blog
 We are looking forward to Enterprise Connect 2024! If you’ve never heard of it, continue reading to find out what it entails and what we’re looking forward to next year.
We are looking forward to Enterprise Connect 2024! If you’ve never heard of it, continue reading to find out what it entails and what we’re looking forward to next year.
 With ChatGPT's assistance, writing IVR scripts has never been easier.
With ChatGPT's assistance, writing IVR scripts has never been easier.
.png?sfvrsn=e27a948_1) ComputerTalk is pleased to announce that we have been scored as a leader against NICE in the Info-Tech Research Group's SoftwareReviews. Continue reading to find out what categories we outperformed NICE in.
ComputerTalk is pleased to announce that we have been scored as a leader against NICE in the Info-Tech Research Group's SoftwareReviews. Continue reading to find out what categories we outperformed NICE in.

